Logystera: Real-Time Metrics, Rules & Alerts from JSON Logs
JSON audit logs (including Vault) → real-time metrics, rules, and alerts. Ingest tens of millions of log events per day with multi-tenant, namespace-aware observability and low-noise alerting. Vault is our flagship use-case, but any JSON log source is supported.

We trimmed alert fatigue by 60% because suppression and bundling are baked into the platform.
Identity-aware metrics finally made namespaces and entities visible across teams.

Grafana was plug-and-play; we shipped tenant dashboards in a day without touching code.

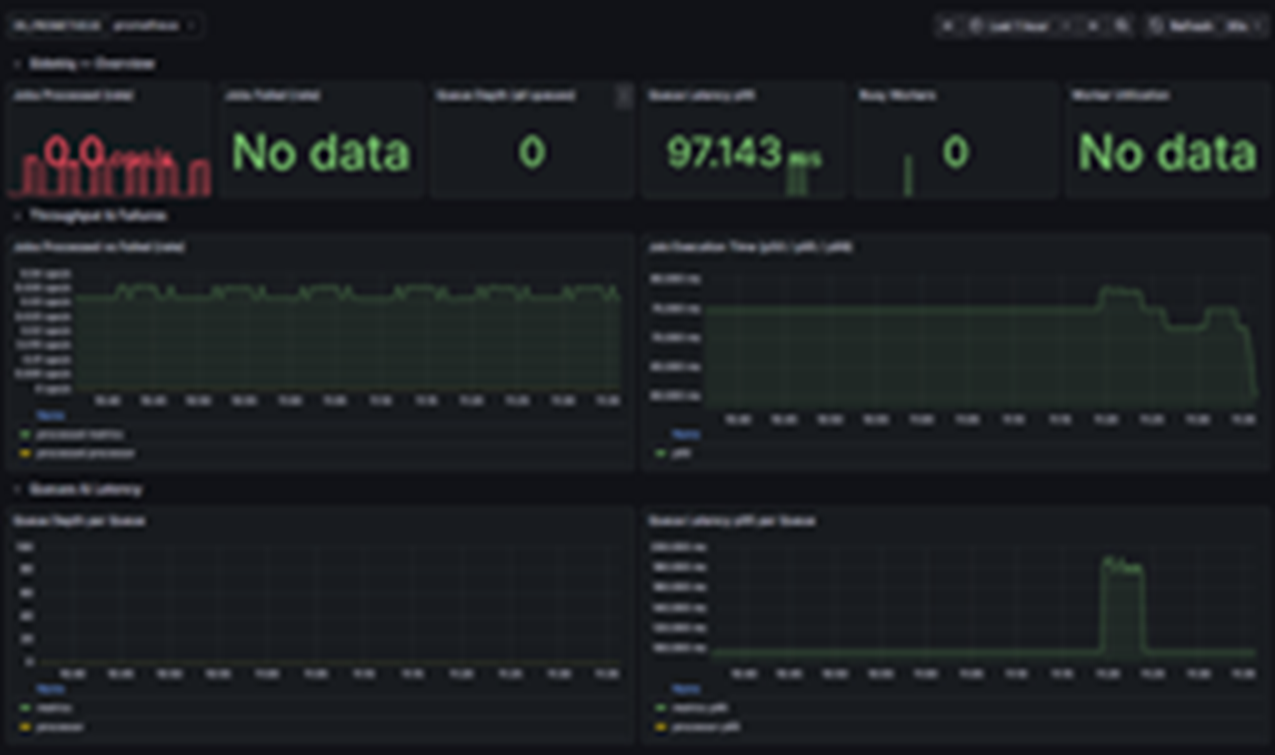
From Log Archaeology to Instant Insight
What changes when Vault audit logs become semantic metrics instead of raw JSON?
Without Logystera
Your Vault audit logs show 42,000 ‘write’ operations yesterday.
- Is that normal? You have no baseline.
- Better grep through 3GB of JSON.
- Hope you're searching for the right patterns.
- Which writes were expected? Which are suspicious?
Time spent: 4+ hours of senior engineer time
Outcome: Maybe you found the issue. Maybe you didn't.
With Logystera
Your Grafana dashboard reveals in 30 seconds:
- ci-service-account → 39,000 writes to
dev/ci-pipeline/*Expected CI behavior - normal - marketing-team → 2,800 writes to
shared/api-keys/*New contractor onboarding - expected spike - external-contractor → 200 writes to
production/database/*⚠️ Investigate immediately
Time spent: 30 seconds
Outcome: Clear action item identified
Built With the Signals You Already Use
Platforms and pipelines we integrate with
Signals, Rules, and Metrics for Your JSON Logs
Logystera extracts high-value operational and security signals from JSON audit logs (including Vault) using real-time ingestion, YAML rule definitions, and Prometheus metrics.
Real-time ingestion pipeline
- File tail, Fluentd, or RabbitMQ with tenant and cluster labels applied at ingest.
- Parallel forwarder/consumer/processor services sized independently.
- Backpressure-aware flow control for bursty audit streams.
YAML rules engine
- Thresholds, sliding windows, suppression, and bundling without redeploys.
- Dynamic labels from any JSON field for precise routing and grouping.
- Versioned rules for auditability and fast rollback.
Multi-tenant isolation
- Namespaces and tenants isolated by default for rules, metrics, and quotas.
- Per-tenant dashboards, alerts, and rate limits to protect noisy workloads.
- Safe for regulated, shared Vault clusters.
Identity-aware detection
- Understands tokens, entities, namespaces, leases, and auth flows.
- Detects privilege jumps, token spikes, and anomalous auth flows.
- Correlates errors and lease events across namespaces.
Prometheus metrics
- Multi-registry /metrics endpoint tuned for low-latency scrapes.
- Counters, gauges, and histograms compiled from YAML metrics.
- Throughput, latency, queue depth, alert outcomes, and registry health.
Alerting pipeline
- Email, webhook, and Slack delivery with retry, dedupe, and suppression.
- Bundling to collapse bursts (e.g., auth failures) into actionable alerts.
- Alert outcomes and suppression state exposed as metrics.
Redis-backed state + parallelism
- Redis stores windows, dedupe keys, suppression lists with <5ms access.
- Sidekiq/worker parallelism for high-volume rule evaluation.
- Detailed worker metrics for capacity planning.
On-prem PKI-ready pipeline
- Runs fully on-prem with no cloud dependency.
- Private PKI for mTLS between agents, services, Redis, and RabbitMQ.
- Configurable for air-gapped and high-security environments.
Why Logystera?
Built for enterprise observability teams that need clarity, control, and predictable rollouts.
Signals over noise
Bundling, suppression, and dedupe so teams act on what matters.
Multi-tenant by design
Namespaces, quotas, and per-tenant dashboards ready on day one.
On-prem ready
Private PKI and no external telemetry for regulated environments.
How It Works
From raw audit logs to clear, low-noise signals with YAML-defined rules and Prometheus metrics.
Send logs
File tail, Fluentd, or RabbitMQ with tenant/cluster labels applied at ingest.
Process
YAML rules and metrics compile into PromQL; suppression and bundling reduce noise.
Observe
Prometheus metrics, Grafana dashboards, and alert delivery with retry/suppression.
Ready to see it in action?
Request a live Logystera walkthrough tailored to your environment.
We will map your namespaces, auth methods, and monitoring into a clear plan with metrics, rules, and dashboards.